What is PGP
PGP (Pretty good Privacy) is the most widely recognized public key encryption program in the world. It can be used to protect the privacy of email, data files, drives and instant messaging.
Traffic on the Internet is susceptible to snooping by third parties with a modicum of skill. Data packets can be captured and stored for years. Even mail servers will often indefinitely store messages, which can be read now or at a future point, sometimes long after the author has changed his or her point of view. Email, unlike a phone call or letter, is not legally protected as private communication, and can therefore be read by third parties, legal or otherwise, without permission or knowledge of the author. Many privacy watchdog groups advocate, if you aren't using encryption, don't include anything in an email you wouldn't want to see published. Ideally this includes personal information as well, such as name, address, phone number, passwords, and so on.
PGP encryption provides privacy missing from online communication. It changes plain, readable text into a complex code of characters that is completely unreadable. The email or instant message travels to the destination or recipient in this cyphered form. The recipient uses PGP to decrypt the message back into readable form. Whether you are concerned about protecting privacy rights, a corporate whistleblower, or a citizen that simply wants to chat with friends without allowing people to 'listen in,' PGP is the answer.
The simple but ingenious method behind public key encryption is based around the creation of a customized key pair. The key pair consists of a public key and a private key. The public key encrypts messages, while the private key decrypts them.
Using PGP, Mr. Able would generate a key pair by entering a real name or nickname to be associated with the keys and a password. The two keys are interlocking algorithms that appear as small bits of text code. Mr. Able can freely share the public key with anyone who wishes to send an encrypted message to him. For example, let's say Mr. Able gives his public key to Ms. Willing. He can copy and paste it into an email and send it to her 'in the clear.'
Ms. Willing receives the public key and copies it to her public key ring in PGP. After she writes an email to Mr. Able, the email is encrypted using the associated public key, obtained from the key ring. The encrypted email is now sent. If someone captures the email en route, or even if it is stored on a server, it will be unreadable.
When Mr. Able receives the email, his private key decrypts the message. Thus the communication is kept private, even though it travels over public channels. The encryption and decryption can be done automatically, as PGP seamlessly interfaces with most major email clients.
To send an encrypted email to someone using PGP, you only need his or her public key. Each public key is unique and works with the associated private key as a key pair. If you encrypt a message with the public key of someone other than the recipient, the recipient will not be able to decrypt the message.
When creating a key pair in PGP, the option exists for your public key to be sent to a public key server. This makes it possible for strangers to send you encrypted mail by simply looking up your public key. SR users would be advised to think carefully however, before uploading their key to a public server. Instead, paste your public key in your profile or at the bottom of your PM's, as well as emailing your public key discretely to handpicked friends and other SR members.
A PGP user can also use his or her private key to digitally sign outgoing mail so that the recipient knows that the mail originated from the named sender. A third party would not have access to the private key, so the digital signature authenticates the sender.
Sensitive data files stored on your hard drive or on removable media can also be protected using PGP. You can use your public key to encrypt the files and your private key to decrypt them. Some versions of PGP also allow the user to encrypt an entire disk. This is especially useful for laptop users in the event the laptop is lost or stolen.
Early versions of PGP were written by Philip Zimmermann and first offered to the public in 1991. PGP is open source and has several different versions available with various opinions about which is best. Some versions of PGP are free for personal use while some are a fully licensed packages for sale. Symantec is now the owner of the official PGP Corporation versions, the latest being PGP Desktop 10.
For our purposes we will be concentrating on the free, open source software packages, the primary being GPG/GnuPG or GNU Privacy Guard.
PGP System Requirements
PGP software, both free and commercial, is available for Windows, Mac OSX and Linux. For the purposes of this FAQ we will limit ourselves to those PGP software packages that are available freely on the Internet, where the only cost for the software is the time you will invest downloading, installing and configuring it.
WINDOWS:
For Windows you will need a 32 or 64 bit version of Windows XP, Vista or Windows 7. So far as hardware requirements, any reasonably current computer should suffice (anything less than 5 years old). For Windows your best opensource product is GPG4win.
OSX:
For OSX you will need a current version of MAC OSX 10.x and a reasonably current Mac workstation or notebook. GPGtools is the OSX compatible version of GPG.
LINUX:
GnuPG works fine on GNU/Linux with x86, alpha, mips, sparc64, m68k or powerpc CPUs.
GnuPG should work fine on any current Linux distribution. GnuPG is open source and available for download from:
The GNU Privacy Guard
Microsoft Windows - GPG4WIN
GPG4WIN Overview
Gpg4win (GNU Privacy Guard for Windows) is an open source PGP encryption software for files and emails.
GNU Privacy Guard (GnuPG, or GPG) is a complete and free replacement for PGP. Because it does not use the patented IDEA algorithm, you can use it without any restrictions. GnuPG is an RFC2440 (OpenPGP) compliant application.
GPG gives your email something that it otherwise doesn't have: privacy. It encrypts your mail so that nobody but the intended person can read it. When encrypted, the message looks like a meaningless jumble of random characters. Additionally, GPG can be used to encrypt datafiles on your machine, protecting sensitive information (such as passwords) from prying eyes.
You can also use GPG to apply a digital signature to a message without encrypting it. This is normally used in public postings, such as Usenet, where you don't want to hide what you are saying, but rather want to allow others to confirm that the message actually came from you. Once a digital signature is created, it is impossible for anyone to modify either the message or the signature without the modification being detected by GPG.
Where to get GPG4Win
GPG is available from Gpg4win - Secure email and file encryption with GnuPG for Windows
Complete installation instructions and documentation are also available from the site. You may also use the following links to download the current version and documentation:
http://ftp.heanet.ie/mirrors/ftp.gpg4win.org/gpg4win-2.1.0.exe
Gpg4win Compendium
Important: If you click on the above links while using TOR, you will be advised that it needs to open an external application to perform the download. This action can potentially remove your anonymity. If you are worried about security, right click the link and copy the link location, then paste it into a regular browser session to complete the download.
GPG4Win Components
Gpg4win is an installer for Windows and contains several Free Software components:
GnuPG
The core application. This is the actual encryption tool.
Kleopatra
A certificate manager for OpenPGP and X.509 (S/MIME) and common crypto dialogs.
GPA
An alternative certificate manager for OpenPGP and X.509 (S/MIME).
GpgOL
A plugin for Microsoft Outlook 2003 and 2007 (email encryption).
GpgEX
A plugin for Microsoft Explorer 32bit (file encryption).
Claws Mail
A complete email application with crypto support.
Gpg4win Compendium
The documentation (for beginner and advanced users), available in English and German.
System Requirements
Gpg4win runs on Windows XP, Vista and 7. Both 32 and 64bit systems are supported.
The Outlook plugin GpgOL is compatible with Microsoft Outlook 2003 and 2007. Outlook 2010 is not supported.
Important: Currently, the Windows Explorer plugin GgpEX works with 32bit Explorer only. It is possible to use the 32bit Explorer on some 64bit Windows. A 64bit update is in progress. All file crypto features of GpgEX on Windows 64bit can be accessed from the file menu of Kleopatra (e.g. File > Sign/encrypt file).
Installing GPG4Win
Download the GPG4Win installer file from the GPG4Win website and save it to your hard drive. Double click the installer file. You will be presented with the GPG welcome screen.
Apple OS X - GPGTools
GPGTools Overview
GPGTools is an open source initiative to bring OpenPGP to Apple OS X in the form of an easy installer package based on MacGPG (see Gpg4win if you're a Windows user). This allows you to sign, verify, and encrypt/decrypt files and e-mails. Read the introduction to get a detailed idea of how PGP works.
Where to Get GPGTools
GPGTools is available from GPGTools. Direct links are as follows:
Download GPGTools - http://www.gpgtools.org/installer/index.html
Introduction to GPGTools - http://www.gpgtools.org/screencast.html
GPGTools FAQ`s - http://www.gpgtools.org/faq.html
GPGTools Components
GPGTools combines the following packages into one installer:
GPGMail
Integrated GPGMail for OS X 10.5 to 10.7, Universal
GPG Keychain Access
Integrated GPG Keychain Access for OS X 10.6 to 10.7
GPGServices
Integrated GPGServices for OS X 10.6 to 10.7
GPGPreferences
Integrated GPGToolsPreferences for OS X 10.6 to 10.7
MacGPG 1
For OS X 10.5 to 10.7 - Intel
MacGPG 2
For OSX 10.5 to 10.7 - Universal
Enigmail Integration
For Thunderbird versions 3 to 8
Installing GPGTools
Using the link provided earlier, download the current version of GPGTools from the gpgtools website. Save the file to a location on your Mac you can easily find. When the download is complete, if the installer does not start automatically, find the install file and double click it to begin the installation.
To keep things simple, when asked what pieces of the software to install, choose all. This will ensure you do not miss something important and have to go back and start over.
Linux - GnuPG
To be completed
GPG4USB Tutorial
This section on GPG4USB was originally Post by: Astor on August 25, 2013
People are still asking me about my GPG4USB tutorial. It was originally hosted on FH so obviously that is gone now. I will probably put it on a hidden service sometime in the future, but I'm not ready for that now. So, I figured I'd post the text here, which should be enough to get people setup.
If you want the screenshots, I found some clearnet mirrors of it. I have nothing to do with these sites.
GPG4USB Tutorial - BeFree
http://hacksociety.net/Thread-Tutor...ncrypt-plain-text-in-emails-communication-etc
And if you don't want to visit clearnet sites, here is the text.
PGP Basics
A lot of people are confused by public key cryptography. A common mistake is to encrypt messages to other people by using your own public key. That is wrong. Here's how PGP works.
You create a pair of keys that are mathematically related to each other, one is public and the other is private. Never share your private key with anyone. Give your public key to your friends. Collect public keys from your friends. Use their public keys to encrypt messages to them. They use your public key to encrypt messages to you. You use your private key to decrypt messages.
PGP is the name of the encryption protocol. GnuPG (GPG) is the name of a program that performs PGP operations. It's like the difference between DOC, a word processor file format, and Word, a propram that creates DOC files. GPG started as a Linux program, but several ports have been made to Windows. GPG4Win is a popular one, but GPG4USB is better. This tutorial shows you how to use GPG4USB.
GPG4USB
Download GPG4USB from the web site [http://gpg4usb.cpunk.de/download.html] and extract the ZIP archive. GPG4USB is designed to be portable, no installation required. You can copy it onto an encrypted USB thumb drive, for example. Launch the program by double clicking on start_windows.exe.
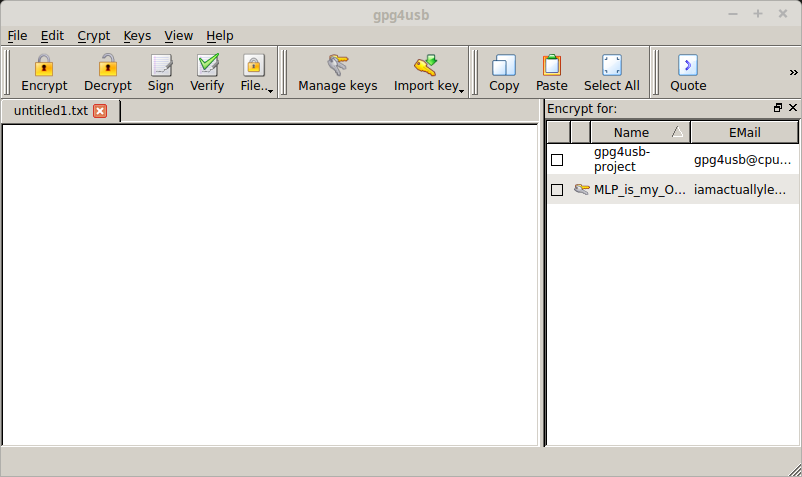
It will ask you to Choose a Language. Then you should see this screen.
At the top is a toolbar for the most common PGP operations, including Encrypt, Decrypt, Sign, and Verify. There's also a place to write messages, and a panel on the right that shows the keys you have imported. At this stage, we see only the developer's key that is distributed with the program.
We don't have a PGP key pair, so we will generate a new one. Select Keys -> Manage Keys.
The Key Management window is where you can import and export keys, but for now select Key -> Generate Key.
Fill out your name and email address. If you want to stay anonymous, don't use your real name or an email address linked to your real identity. This information is viewable by anyone who imports your public key. You can set an expiration date or select Never Expire. There's debate about whether it's better to let a key expire or not, but most keys are set to never expire.
Important: increase the Key Size from the default 2048 bits to 4096 bits. Also, set a strong password, which is used to symmetrically encrypt your private key. If someone steals your private key, a strong password will be the only thing preventing them from decrypting your messages.
It may take several minutes to generate the key pair. The program collects entropy from your computer, so doing random things speeds the process along. You can browse the web or mash on your keyboard.
When it's done, you'll see your key listed in the Key Management window. You can close the window and return to the main interface.
Next you want to import public keys from your friends. Select Import Key from the toolbar. You have several options: import from a file, the clipboard, or a key server. If you want to stay anonymous, you should never publish your keys to or download other people's keys from a key server. The easiest option is to import from the clipboard. Highlight a public key in an email or forum post, right click and select 'copy' to put it in your clipboard.
Important: make sure you highlight the entire beginning and ending lines, with all five dashes on either side of the text:
-----BEGIN PGP PUBLIC KEY BLOCK-----
-----END PGP PUBLIC KEY BLOCK-----
A common mistake is to miss the first or last dash when highlighting. PGP programs won't recognize a public key block without all the dashes.
After copying a public key to the clipboard and selecting Import Key -> From Clipboard, you'll see some details about the key. Click OK to finish importing.
To copy your public key, so you can give it to other people, open the Key Management window and check the box next to your key, then select 'Export to Clipboard'. You can paste your public key into emails, forum posts, etc. Remember to include the beginning and ending lines with all five dashes. You can also choose 'Export to File' and it will create an ASCII armored text file (*.asc). This is a regular text file that can be viewed with any text editor.
Now let's encrypt a message.
Write your message in the text area, then select recipients by checking the boxes next to their keys. In this case, I've selected the GPG4USB developer key. It's common practice to include yourself as a recipient, so you can decrypt the message later if you need to.
Click Encrypt in the toolbar. The plain text will be transformed into an encrypted PGP message.
To send this message, copy the entire block, with the beginning and ending lines, and paste it into an email, forum post, etc.
To decrypt a message, paste it into the text area and click Decrypt. GPG4USB should automatically detect the key that it was encrypted to and use it to decrypt the message. You will have to enter the password for your private key.
Another common procedure is to sign a plaintext message so that others can verify you really wrote it. To do that, write a message and check the box next to your key, then select Sign in the toolbar. The opposite of this is to verify someone else's signature. Copy the entire signed message block into the text area and click Verify.
Lastly, it's a good idea to back up your private key. If you lose it, you won't be able to decrypt messages and they will effectively be lost forever. Right click on your key in the right panel and select 'Show Key Details'. You'll see the dialog above. Click 'Export Private Key' and save the file in a secure location.
PGPTools for MacOS tutorial
The following information regarding PGPTools for MacOS was originally written by Guru on the previous Silk Road forums
GPGTools is highly version dependent -- depending on which version of OS X you have, it may or may not work as expected.
-If you have Leopard (10.5) then you're pretty much out of luck. Your only option then will be using the command-line.
-If you have Snow Leopard (10.6), Lion (10.7) or Mountain Lion (10.8), the following instructions should be sufficient to allow you to get up and running.
*Download and install GPGTools: http://nightly.gpgtools.org/GPGTools_Installer-trunk.dmg
I'm assuming you've aready done that.
-Once you have installed GPGTools, what you want to do is to go into System Preferences --> Keyboard --> Services.
-Scroll down until you find the following entries. Be sure to put a check mark in the boxes to activate each keyboard shortcut.
Keyboard shortcuts:
OpenPGP: Decrypt Selection: Shift-Command-D
OpenPGP: Encrypt Selection: Shift-Command-E
OpenPGP: Import Key from Selection: Shift-Command-I
OpenPGP: Insert My Fingerprint: Shift-Command-F
OpenPGP: Insert My Key: Shift-Command-K
OpenPGP: Sign Selection: Shift-Command-R
OpenPGP: Verify Signature of Selection: Shift-Control-V
Remember, these shortcuts only operate on highlighted or selected text.
-To copy your key to a TextEdit document, open up TextEdit, so you have a blank document open. Then you can use the Insert My Key command, Shift-Command-K -- this will bring up a little dialog box, where you can choose your key from the drop-down box; click Choose Key, and the key will be inserted into your TextEdit document.
-You can then use Command-A to highlight the key, and Command-C to copy it to the clipboard. You can then use Command-V to paste your public key into a PM (or an email) for example.
N.B.: To properly be able to import PGP messages/keys into GPGChain (via TextEdit) you
need to change the default on TextEdit from .rtf to plain text. You can do
that through the Format menu, or you can go through the main configuration
menu, accessible by using Command-comma. Ensure the plain text radio button
is selected.
*Also ensure that the following are UNCHECKED in TextEdit preferences:
smart quotes, smart dashes, smart links.
To select text within TextEdit, use Command-A to highlight the entire
document, or use your mouse to selection the section that you want to
verify/sign/encrypt/decrypt. It is highly recommended that you use only
plain-text, as opposed to Rich Text (.rtf) format. Use Command-comma to
bring up Preferences and ensure that the plain text radio button is
checked.
Once your text is highlighted in TextEdit, (by pressing Comand-A) you then
encrypt using Shift-Command-E. You will then be presented with a list of
keys to encrypt to, that you have added to your PGP keyring:
Other Commands You May Need:
OpenPGP: Decrypt File: Control-Command-D
OpenPGP: Encrypt File: Control-Command-E
OpenPGP: Sign File: Control-Command-S
OpenPGP: Verify Signature of File: Control-Command-V
-Once you have setup these shortcuts, you can begin using GPG.
Copy Usb License Key. Our built-in antivirus scanned this Mac download and rated it as virus free. The bundle id for Gpg Tools for Mac is com.tomsci.GpgTools. The application lies within Security Tools, more precisely General. This free software for Mac OS X is a product of gpgtools. The most popular versions of Gpg Tools for Mac are 2014.11, 2011.07.11 and 2011.07. Gpg4usb is not available for Mac but there is one alternative that runs on macOS with similar functionality. The most popular Mac alternative is GPGTools, which is both free and Open Source.If that doesn't work for you, our users have ranked 4 alternatives to gpg4usb, but unfortunately only one is available for Mac.
Hi there, dansk12345,Gpg4usb is a very easy to use and small portable editor to encrypt and decrypt any text-message or -file you want. Our aim is, to give anyone the possibility to send and receive secure encrypted messages anywhere - on any computer out there, no matter if Microsoft Windows (TM) or Linux is running on it.
 Thanks for using the Apple Support Communities. From your post, I understand that you are trying to set up a GPT (GUID Partition Table) with your flash drive. I'm happy to help!
Thanks for using the Apple Support Communities. From your post, I understand that you are trying to set up a GPT (GUID Partition Table) with your flash drive. I'm happy to help!The 'Make sure that your storage device is properly formatted' section of the
 How to set up and use an external Mac startup disk article provides the following instructions on setting up GPT:
How to set up and use an external Mac startup disk article provides the following instructions on setting up GPT: Make sure that your storage device is properly formatted
For best results, your external hard drive, thumb drive, SDHC or SDXC card, or other storage device should be formatted as Mac OS Extended, not FAT, ExFAT, or NTFS. And to function as a startup disk, it needs to be using a GUID partition map. Here's how to check:
- Connect your external storage device to your Mac.
- Choose Apple menu () > About This Mac, then click the System Report button. Or hold down the Option key and choose Apple menu > System Information.
- Select Storage from the sidebar, then select your storage device from the list of volumes. Make sure that the Partition Map Type shown for your storage device is GPT (GUID Partition Table):
If your storage device isn't using a GUID partition map, you can follow these steps to create one with Disk Utility.This deletes all of the data stored on your device.
- If you're using OS X El Capitan or later, select your external storage device in Disk Utility. (Select the disk name, not the volume name indented beneath it.) Then click Erase and choose the GUID partition map scheme and any Mac OS Extended format before erasing.
- If you're using OS X Yosemite or earlier, select your external storage device in Disk Utility. (Select the disk name, not the volume name indented beneath it.) Click the Partition tab, select your partition, then click the Options button. Select GUID Partition Table before partitioning.
Gpg4usb Mac Os High Sierra
Have a great day!Gpg4usb On Mac
Aug 27, 2017 4:38 PM